|
Getting your Trinity Audio player ready...
|
Cyber attack modeling is an approximation of adversarial threats against a computer system. Cyber attack models are created to identify and simulate attacks against security environments, using likely adversary techniques and attack paths. By modeling attacks, defenders can better understand the behavior, tactics and objectives of adversaries and can take steps to remediate any vulnerabilities within their environments.
Cyber attacks continue to increase in number and sophistication each year, forcing security professionals to expend enormous efforts protecting their critical assets. Botnets, viruses, trojans and other malicious software attacks result in billions of dollars in annual losses for global enterprises and governments.
With new forms of malware emerging and attackers becoming better resourced and more creative, security teams need tools that allow them to anticipate likely attacks, identify vulnerabilities and remediate any problems that are uncovered. The cyber attack model is one of the most effective methods for accomplishing this task.
This approach not only helps shine a light on existing security problems within an environment, it also allows defenders to understand the characteristics of attacks, the methods by which they are executed and the behavior and goals of the adversary launching the attack.
The means attack modeling plays a critical role in providing a perspective on how attacks can be stopped in a coordinated and effective manner.
Deterring Corporate Cyber Attacks Through Modeling
When managing cybersecurity risk, organizations often engage in threat modeling, risk assessment and attack modeling. Threat modeling deals with the possibility of a negative event occurring. Risk assessment details how likely it is that this threat will cause damage. Attack modeling deals with precisely how vulnerabilities are exploited to create this damage. In practice, threat and attack modeling concepts are sometimes used interchangeably, and some modern security solutions incorporate both elements within a single implementation.
In the world of cybersecurity, it is very difficult to protect against attacks effectively without understanding where vulnerabilities lie. By modeling attacks, defenders gain visibility into the presence and severity of vulnerabilities that may have otherwise remained undetected.
Simulating cyber attacks in a controlled environment is one of the most effective attack modeling implementations. Cyber attack simulation tools — such as breach and attack simulation platforms — allow organizations to mimic the techniques and tactics of adversaries across likely cyber attack vectors. By simulating adversary behavior across the attack chain, defenders can adopt the mindset of attackers and pinpoint the precise vulnerabilities that exist within a security environment.
Many solutions that incorporate cyber attack modeling will provide prioritized remediation guidance after vulnerabilities have been identified. By launching simulated attacks, uncovering security gaps and then offering ranked recommendations, these tools can help organizations stay one step ahead of attackers.
Moving organizational security from a purely reactive posture to one that aggressively (and often continuously) probes for vulnerabilities based on known attacks is a hallmark of this approach. By engaging in attack modeling, it is possible to gain deeper insight into the vulnerability level of a security environment and understand the behavior and objectives of adversaries. Ultimately, it then becomes possible to deter cyber attacks or handle incoming attacks in a carefully planned and responsive fashion.
Best Practices of Attack Modeling
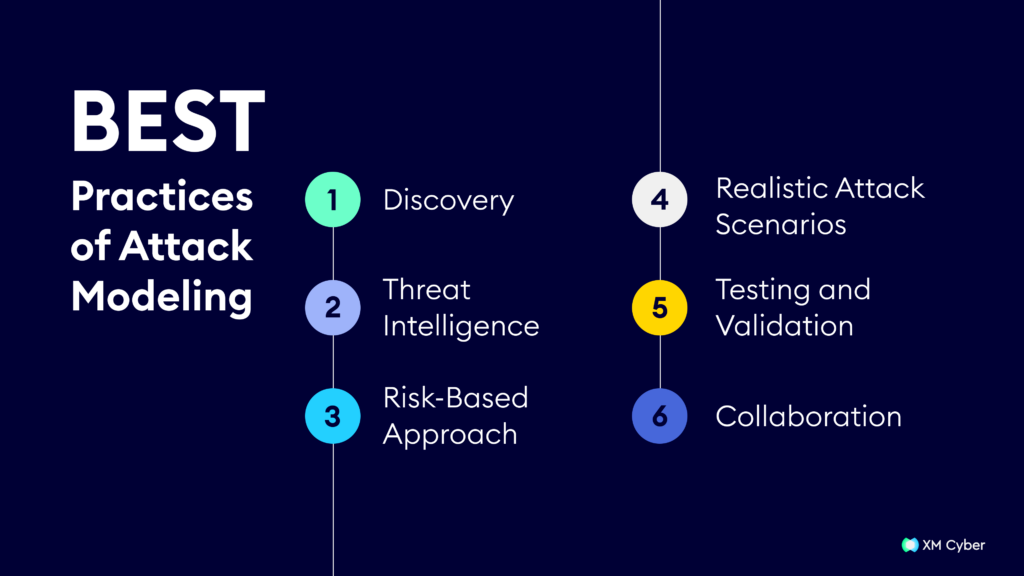
Cyber attack modeling involves creating representations of potential cyber threats and assessing their potential impact on an organization. Employing the following best practices in cyber attack modeling enhances both cybersecurity preparedness and response:
- Discovery – A comprehensive understanding of the organization’s assets, vulnerabilities, and potential threat landscapes is essential. This involves identifying critical assets, analyzing existing vulnerabilities, and staying informed about emerging cyber threats. Regularly updating this information ensures the attack model remains relevant and is adapting to evolving risks.
- Threat Intelligence – Leveraging up-to-date threat intelligence feeds helps in incorporating real-world scenarios into the attack model. This allows organizations to simulate attacks based on current threats, enabling more accurate risk assessments and proactive defense strategies.
- Risk-Based Approach – Adopting a risk-based approach ensures that cyber attack modeling aligns with the organization’s overall risk management strategy. Prioritizing risks based on their potential impact allows for more resource-efficient and cost-effective mitigation efforts.
- Realistic Attack Scenarios – Cyber attack modeling should simulate a diverse range of potential threats, including advanced persistent threats (APTs), insider threats, and various attack vectors. This diversity provides a more holistic view of an organization’s cyber resilience.
- Testing and Validation – Regular testing and validation of the cyber attack model are essential. Conducting simulated exercises activities help identify weaknesses in the existing security posture and improve incident response.
- Collaboration – Fostering collaboration and communication among different departments within an organization is vital. Cyber attack modeling should not be confined to the cybersecurity team alone; input from IT, risk management, and other relevant departments enhances the model’s accuracy and effectiveness.
By adhering to these best practices, organizations can develop robust cyber attack models that contribute significantly to their overall cybersecurity resilience and readiness.
What is Cyber Threat Modelling?
As mentioned above, cyber threat modeling is essentially identical to cyber attack modeling, and the terms are often used interchangeably. The core objective of cyber threat modelling is to simulate potential cyber threats and understand their impact on an organization’s assets. In both cases, the focus is on anticipating and preventing cyber threats before they materialize.
The cyber threat modelling process involves identifying assets and their value, evaluating vulnerabilities, defining potential threat actors and their capabilities, and determining possible attack paths. By creating models that simulate these scenarios, organizations can better understand their security posture and implement effective countermeasures.
The Four Methods of Cyber Threat Modeling
There are four primary methods of cyber threat or attack modeling, each offering a distinct approach to analyze and address security risks.
- STRIDE Model – The STRIDE model, developed by Microsoft, categorizes threats into Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It provides a structured approach to identifying and addressing these six dimensions of cybersecurity threats.
- DREAD Model – The DREAD model evaluates threats based on Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability. By assigning scores to each criterion, it aids in prioritizing and focusing on critical threats, emphasizing impact, ease of exploitation, and likelihood of detection.
- VAST Model – The Visual, Agile, and Simple Threat (VAST) modeling approach is designed for rapid threat modeling, emphasizing simplicity and collaboration. It encourages the use of visual aids, diagrams, and collaborative sessions for quick threat identification, making it suitable for dynamic development environments.
- Attack Trees – Attack trees represent hierarchical structures illustrating potential attack paths and outcomes. Starting with a root attack goal, the tree branches into different attack scenarios, providing a visual representation that aids in understanding the complexity of potential threats and identifying vulnerable points within a system.
Each of these threat modeling methods offers a unique perspective and approach to understanding and mitigating cybersecurity risks. The choice of method depends on factors such as organizational needs, system complexity, and the desired level of detail in threat analysis.
How Does Threat Modeling Work?
Threat modeling is a systematic process that works to identify, assess, and mitigate potential cybersecurity threats to an organization’s systems. The goal is to proactively enhance cyber security by understanding and addressing vulnerabilities. The process typically involves the following key steps:
- Define the System – Identify and understand the components and boundaries of the system being assessed. This includes hardware, software, data, personnel, and the interactions between these.
- Identify Assets and Resources – Enumerate and classify the system’s critical assets and resources. This includes sensitive data, software applications, infrastructure components, and any other elements vital to the organization.
- Enumerate Threats – Brainstorm and list potential threats that could exploit vulnerabilities within the system. Common threat categories include unauthorized access, data breaches, denial of service, and more.
- Prioritize Threats – Evaluate and prioritize the identified threats based on their potential impact and likelihood. This helps in focusing resources to address the most critical risks first.
- Develop Countermeasures – Propose and implement countermeasures to mitigate the identified threats. This could involve implementing security controls, improving access controls, or enhancing encryption methods, for example.
- Iterate and Update – Threat modeling is an iterative process that evolves with changes to the system, technology, or threat landscape. Regular updates ensure that the model remains relevant and effective in addressing emerging risks.
In Conclusion
The sophistication of advanced persistent threats and the growing complexity of cloud security management leave defenders with significant challenges. Cyber attack modeling is one of the most effective methods for identifying and remediating vulnerabilities. By modeling attacker behavior, defenders can reach a deeper understanding of their tactics and goals. Adopting the mindset of the attacker in a controlled environment enables defenders to gain a deeper perspective on how attacks are likely to unfold, then take the necessary steps to either deter attacks or limit any damage caused by their execution.


