|
Getting your Trinity Audio player ready...
|
With many organizations making their shift to the cloud, a clear “cloud first” mentality has become prevalent among security professionals. And not so surprisingly, “cloud first” has started to imply “on-prem second”.
But this is a mistake.
The thing is that the shift to the cloud does not mean that on-prem threats have somehow lessened or become all of the sudden unimportant. Quite the opposite, in fact. As organizations move more and more critical assets and processes to the cloud, assets may be even more exposed than they were previously.
As a proof, in our own recent research we detected exploitable attack paths from on-prem to cloud platforms in 71% of organizations. What’s more shocking is that our research found that after accessing cloud environments, 92% of critical assets lie just one hop away. ????
On-Prem Dangers are Still Acute
This is why it’s impossible to fully protect cloud assets without protecting on-prem environments, and vice-versa. Attackers who are able to successfully compromise corporate networks likely won’t find it difficult to expand their access to other environments and all too often, on-prem essentially leaves nice open pathways to cloud environments. To further illustrate the point, a series of recent attacks publicized by Microsoft initially targeted on-premises Azure AD Connect, which resulted in the destruction of cloud resources.
What’s more, our research also found that:
- Organizations typically have 11,000 security exposures attackers could exploit, and some larger enterprises have over 20x that number!
- Attackers can access 70% of critical assets in on-prem networks in just three steps.
- Endpoint detection and response capabilities cover fewer than half of all devices in 38% of firms.
Clearly, organizations need to devote more mindshare to addressing on-prem threats, alongside their efforts in the cloud. One way of approaching this is to examine the root issues that make it increasingly easy for attackers to compromise on-prem networks. By analyzing common on-prem attack techniques, how attackers can pivot to the cloud (and back), and how these steps combine to form attack paths, defenders can make it more challenging for adversaries to infiltrate systems.
Crucial to Pivot Both Ways
There are many ways an attacker can pivot from on-premise to cloud, for example:
- Direct network attack – Systems running in the cloud that are directly connected to the back office network or data center can be attacked like any traditional on-prem resource
- Azure pass-through authentication compromise – Compromise of a server running Microsoft Azure AD Connect on-prem can lead to Azure compromise
- AWS access token stealer – An attacker can steal AWS access tokens from an endpoint
- GCP compromised service account key – An attacker can obtain the CLI and SDK service account keys that are stored in cleartext on an endpoint
- Azure PRT token stealer – Primary Refresh Token can be stolen from an endpoint
To understand how these attacks work, and how to stop them, it’s illuminating to pick apart the key steps of a sample attack path. Take a look at the diagram below:
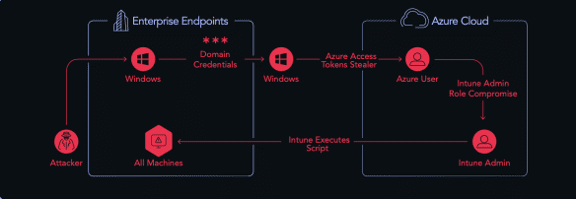
The steps of this attack are as follows:
- Stealing domain credentials – Once the attacker has a foothold, they steal domain credentials on a Windows endpoint that have been left behind after an RDP session.
- Lateral movement with domain credentials – The attacker uses these domain credentials to laterally move to another device.
- Stealing Azure access tokens – The attacker obtains Azure tokens, which are stored in a specific path on Windows, Linux or Mac endpoints.
- Azure user compromise – Using the Azure tokens, the attacker compromises an Azure user account.
- Intune admin role compromise – The Azure user compromised has Azure Intune Admin privileges – which the attacker now has, too.
- Execute scripts on all machines – Leveraging his Intune admin privileges, the attacker can now execute scripts on all cloud and on-prem machines.
Step six is crucial. The last steps an attacker takes are frequently steps that cannot be mitigated. This means that if you don’t catch the earlier steps – whether they’re on-prem or in the cloud – you may not succeed in preventing the attack at all. As in the above sample, real world attacks paths move between environments – frequently from on-prem to the cloud. The reason? Attackers have a better chance of compromising devices on-prem – for example, via phishing.
This means that cloud-only security tools like CNAPP actually come in midway through the story. They only see data representing steps 4-6 in the attack path above, and these are all apparently legitimate actions. It’s only steps 1-3 that subsequently make steps 4-6 a high risk. Therefore, in this case – and many others – if you’re not seeing the on-prem part of the attack path, you’re not seeing the full attack picture. (Want to see more really eye-opening attack paths in action? Check out this ebook chock full of attack paths we found and how they were remediated.)
The Bottom Line
Dedicated cloud security platforms like CNAPP, CSPM and CWPP were adopted rapidly in recent years, as organizations moved more and more workloads to the cloud. Yet these solutions often neglect to address how remaining assets in the on-prem environment can impact the cloud – and vice versa.
To get full visibility of the risk to cloud workloads, organizations need to understand the attack paths that can be created from on-prem to cloud and back again, mitigating issues early in the chain to protect their cloud investments.



