TRUSTED BY:
This is the average number of exposures that demand your attention each month.
What should you fix first?
This is the average number of exposures that demand your attention each month.
What should you fix first?
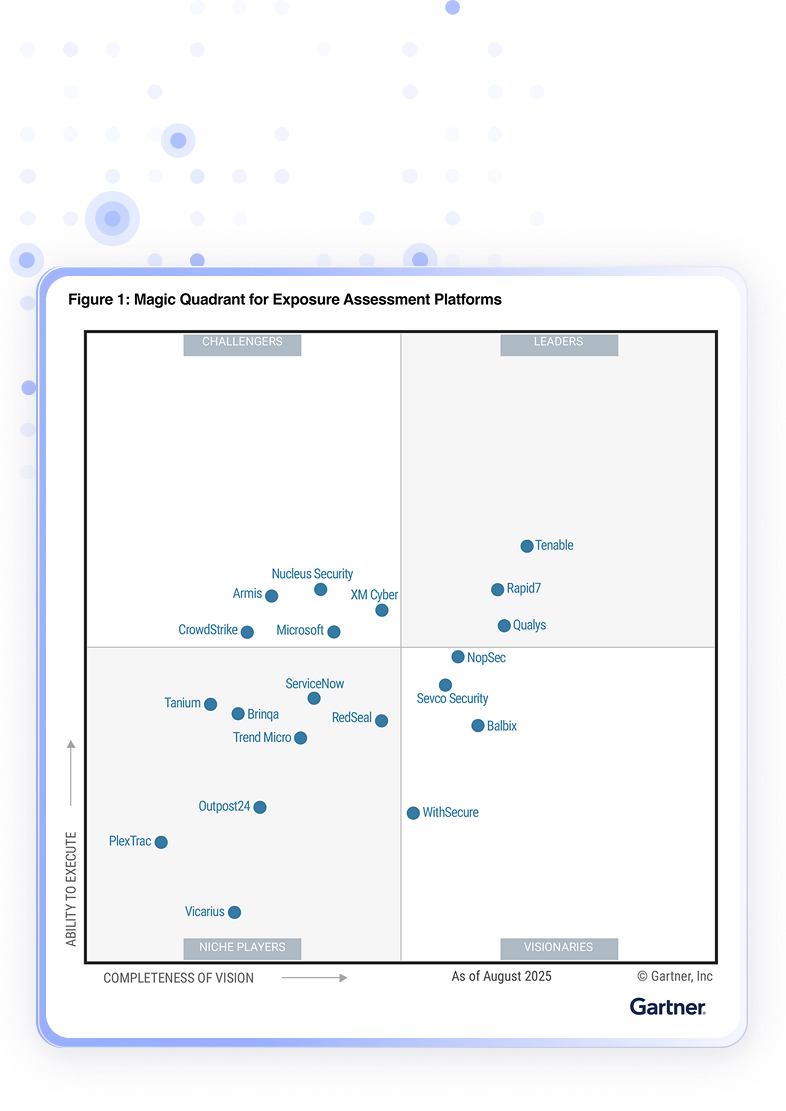
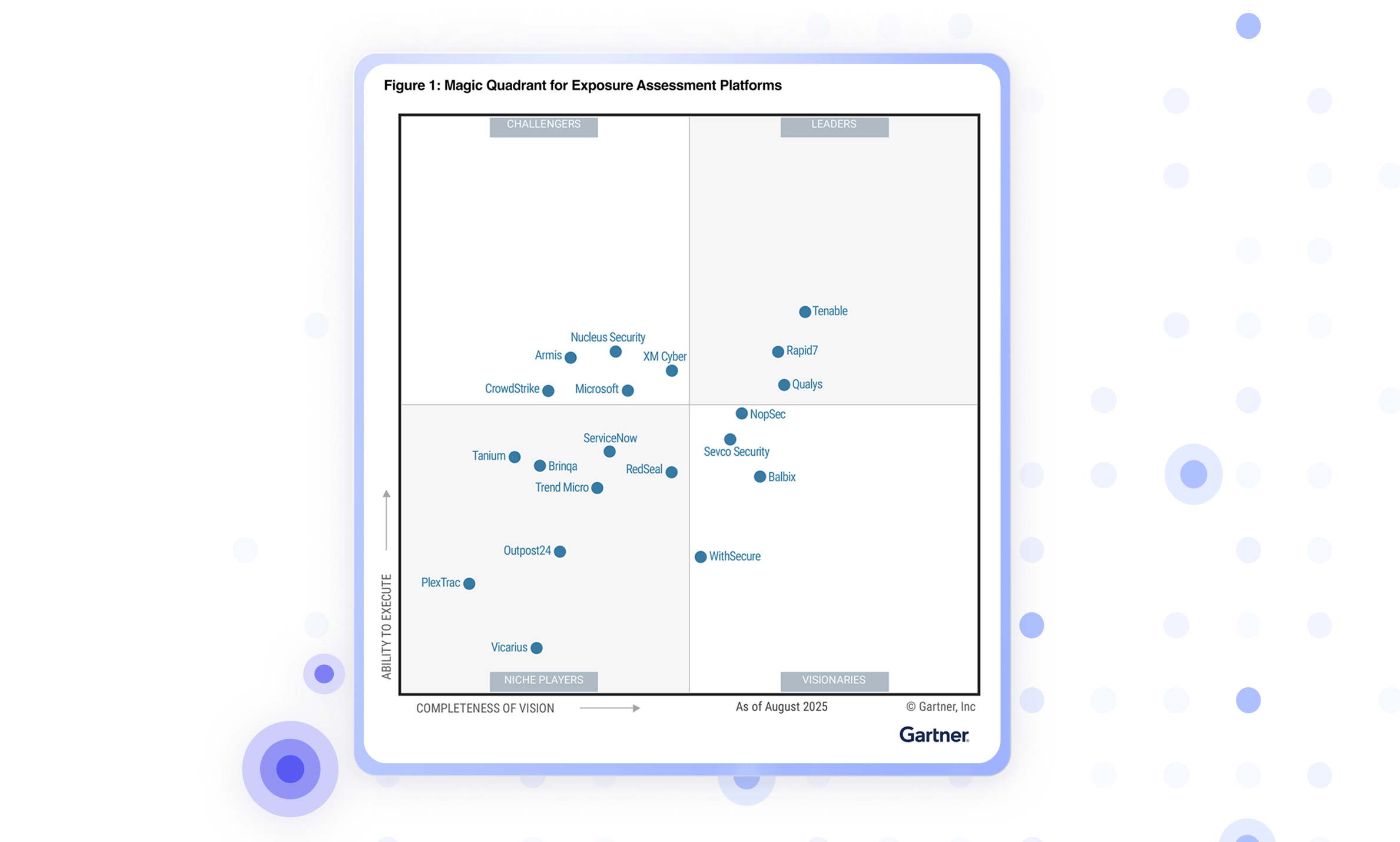
IT’S TIME FOR A NEW APPROACH
See All Exposures, Fix What's Critical
XM Cyber's Continuous Exposure Management Platform cuts through the endless lists, providing graph-based context to prioritize the exposures that put your critical business assets at risk.
Gain a unified view of your entire attack surface, revealing how diverse exposures interconnect to create attack paths. With risk-based context to the business, you can identify and fix the exposures with the highest remediation ROI to optimize security posture and improve resource efficiency.
Prevent High-Impact Attacks
Continuously secure your critical assets from a combination of attack techniques.
Gain Remediation Efficiency
Stop wasting resources on fixes that don't impact risk. Remediate what matters most.
Report Meaningful
Risk
Confidently answer executive questions with a shared understanding of business-critical risk.
XM Attack Graph Analysis™
Fix What Matters with Business Context
XM Attack Graph Analysis™ gives you clear, context-based insights into all exposures from your external attack surface across your hybrid infrastructure, to your business-critical assets. This means Security and IT teams can align on the smallest number of exposures that need to be addressed for optimal risk reduction and better security outcomes.
Explore the platformUSE CASES
Secure Your Business Initiatives
Eliminate Risk Across the Full Attack Surface With Continuous Exposure Management
What Our Customers Say
-
The product is easy to deploy, easy to handle and configure, and gives great and important insights from the attacker׳s point of view.
IT Security and Risk Management - Manufacturing
-
This tool allows you to define quick-win remediation but, more importantly, focuses on compromising paths to its most critical assets.
IT Security and Risk Management -
Banking -
Best CTEM feature solution currently on the market. The usability and product features are innovative to me and work well.
IT Security & Risk management-
IT Services
Total Economic Impact Study™ of XM Cyber
394%
Return on investment, with payback in under 6 months
$12.4M
Reduction in remediation, fines, lost revenue, and brand reputation costs
$1.4M
Reduction in costs associated with penetration testing
90%
Reduction in the likelihood of experiencing severe breach