Almost all of us have been the victim of a friendly April Fool’s joke. You know the setup: We’re led to believe an outrageous premise, the joke is revealed, and everyone has a nice laugh. It’s an enduring annual tradition.
It sounds ludicrous, but each year millions of people fall victim to popular April Fool’s Day hoaxes, including left-handed toilet paper, the redefinition of Pi, and all of Google’s annual April Fool’s Day tricks.
Viewed in that context, it suddenly doesn’t sound so strange that people continually fall victim to the same tricks deployed by hackers, who have their own wide array of methods of fooling people, such as phishing attacks and data breaches that leave security professionals wincing in pain, rather than groaning good-naturedly.
Ultimately, we fall victim to hacks and hoaxes for the same reason: A lack of vigilance and anticipatory awareness.
On this April 1, now is the perfect time to revisit some of the most effective things an organization can do to avoid being fooled — and suffering serious financial and reputational harm.
Smart IT Hygiene Doesn’t Make Organizations Foolproof…but it Does Make Them Fool-Resistant
Sometimes the simplest thing you can do is the most impactful. In the case of spreading disease, scrubbing our hands with soap and water works better than almost anything else. In the realm of cybersecurity, basic IT hygiene plays an equally powerful role. Consider this: While many organizations are concerned about sophisticated Advanced Persistent Threat attacks (and rightly so), the vast majority of attacks are relatively unsophisticated. The National Security Agency reports that 93% of all attacks could be stopped with basic cyber hygiene practices.
With that in mind, let’s run down some of the essentials of a smart IT hygiene regimen:
- Strong password management. Passwords should be varied among accounts and complex enough to prevent brute force cracking. For most people, keeping up with constant password change requests and remembering exotic strings of letters, numerals and special characters is too much to ask, however. Hackers understand this password maintenance fatigue and exploit it. To avoid being fooled (or overcome by the need to create and juggle dozens of strong passwords), a password manager is needed. A secure password manager can largely automate the process of creating and maintaining individual passwords, and store these passwords within an encrypted vault.
- Adopting multi-factor authentication for your applications and accounts. Using Google Authenticator or a similar application can provide a robust added layer of security to support your password management. These applications generate unique one-time codes that are used to grant access to each of your accounts when used in conjunction with your password. Multi-factor isn’t a magic solution for perfect protection, however. Hackers have been able to bypass some multi-factor authentication programs, with SMS-based authentication being especially vulnerable.
- Streamline admin privileges wherever possible. Fools rush in to award admin privileges where more cautious IT managers fear to tread. Admin privileges tend to bloat over time, so it’s important to prune the list regularly. If people have moved on to new positions or projects and admin access is no longer a significant need, revoking these permissions can help improve cyber defense by limiting attack points.
- Remove unauthorized applications. By introducing a whitelist of approved applications, you erect a strong barrier preventing malicious executable files or programs from running. If you’re not on the whitelist, you can’t get in. It’s the digital version of trusting no one and nothing you hear on April 1.
- Drop joint Wi-Fi connections for employees and guests. Instead, create a dedicated network for guests and ensure that only approved devices and users can access your company’s private network.
- Invest in rigorous and regular IT hygiene training. William Shakespeare famously said, “A fool thinks himself to be wise, while a wise man knows himself to be a fool.” In the context of cybersecurity, Shakespeare’s aphorism can be read as a warning against complacency and overconfidence. Successful attacks often come from an angle that we completely fail to anticipate. One way to mitigate this: Use regular and rigorous training to increase vigilance and awareness. Embrace skepticism rather than confidence.
While following routine practices like these helps keep computing systems safe, we don’t want to extend the cyber hygiene/persona hygiene metaphor too far. The human body has a powerful and complex immune system that generally bails us out from acquired infections, even if we’ve been lax on hand washing. Computers, on the other hand, have mere circuits. It takes the combined efforts of skilled security professionals and cutting-edge tools to fend off viruses and close down cybersecurity attack vectors.
Don’t Get Fooled Again: How Cybersecurity Simulation Reduces the Risk of a Painful Data Breach
Comprehensive hygiene, both in the IT and personal realms, is smart preventative practice. Yet sometimes your system, human or cyber, needs a bit of a boost to stave off infections.
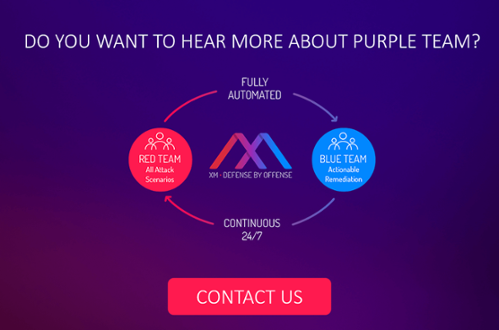
Breach and attack simulation technology plays that role by allowing organizations to mimic the techniques used by today’s attackers. XM Cyber’s breach and attack platform works by launching countless simulated attacks against a security environment. These simulations expose vulnerabilities that threaten an organization’s critical assets. Once they are identified, our breach and attack solution provides prioritized remediation recommendations to help quickly close these gaps.
In this sense, our solution works much like conventional penetration testing. Yet while traditional penetration testing is highly manual and resource-intensive, our solution is automated and efficient, providing 24/7 protection and unparalleled visibility into the true state of an organization’s defenses.
Breach and attack simulations are also unique in their ability to allow defenders to assume the mindset of an attacker and peer into their bag of tricks. As any April Fool’s prankster knows, it’s almost impossible to fool someone who is actively anticipating being tricked.
On April Fool’s Day, organizations that want to avoid a nasty surprise should consider refreshing their IT hygiene — and supporting their systems with continuous, automated protection.
Marcus Gilban is Head of Marketing Communication, XM Cyber
Related Topics