The volume of IT threats and the surprisingly unsophisticated means to wreak damage are putting unprecedented pressure on security teams. With limited time and manpower, they need the right combination of visibility, intelligence, and context to find threats in real time and remediate them.
The newly released “2019 High-Fidelity Security” research report outlines issues with data collection and use habits from 250 companies operating worldwide in 25 different industries, showing how such gaps can impact an organization’s ability to maintain high-fidelity security.
Automation is a must-have, according to the CIOs, CTOs, IT VPs, and directors who responded to the survey. Nearly 90% of them believe that the automation of tasks, actions, and/or analysis to achieve network security program goals for breach detection is either “important” or “very important.” However, only 40% have already implemented automated processes.
Security Bravado vs. Real Efficacy
The research also identified that 78% of organizations are less than wholly comfortable with their current cyber risk, and 12% are moderately to very uncomfortable with their cyber risk, according to
David Monahan
, Managing Research Director of Security and Risk Management at Enterprise Management Associates (EMA), who led the survey.
“Although 87% of organizations indicate they feel their current controls are effective in protecting critical assets, this seems to present more of a security bravado than a real efficacy, especially considering 29% of organizations indicated they are not able to identify or stop a compromise until somewhere between the lateral movement phase and after the event—a.k.a., way too late,” wrote Monahan in a post-survey report. “Only 28% of organizations believe they are fully effective in proactively identifying security control gaps,” he added.
Key Takeaways
Over 68% of organizations believe they need more frequent security control testing, with those performing tests more frequently than annually being the biggest proponents of doing so. Respondents recognize that more automation is needed to find and close control gaps and perform incident response and remediation.
To help you take advantage of the survey-based research, EMA selected some excerpts from the “Unlocking High Fidelity Security 2019” research report released by EMA in May 2019.
- Automation in Operations
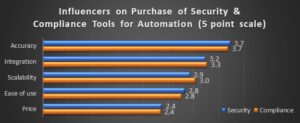
The average enterprise of between 5,000 and 10,000 personnel has to monitor multiple times that number of systems and more than ten times that number of alerts. At these levels of scale, automation is crucial for success. In the survey, participants were asked their primary influencers on choosing automation tools. The results are visible in the chart.
“With automation, the accuracy of the system is most important. If automation brings results faster, then having those outcomes be correct is the most important factor. After accuracy, the types of integrations into the automation system are crucial for acting over a broader scope of problems and driving scalability in the types and scopes of problems that can be addressed. Even though the price was last on the list, that does not mean money is no object. For the time being, budgets are strong and growing, so money is less of a concern than overcoming other operational issues. Decision makers are still price-conscious but exercise more flexibility,” reads the report.
- The Importance of Breach Attack Simulation (BAS) and Automation
Beyond penetration testing and red teams, a new category of security solutions has emerged. Breach and Attack Simulation tools perform automated security testing: some challenge the existing security infrastructure and some model attack chains to identify the most likely path an attacker would use to compromise an environment.
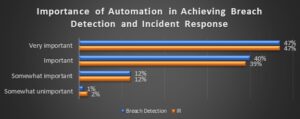
BAS products are becoming more mainstream and have begun transforming the security testing landscape. The following chart displays both the perceived importance of automation for breach simulation and automation in general for achieving SecOps goals.
“Automation as a functional need for security is very important. Tools that provide more automated and automatic functionality will continue gaining market penetration. EMA also expects to see the percentages in the following graph move up into ‘very important’,” according to the report.
- Vulnerability Testing, Penetration Testing, and BAS
Another excerpt states that penetration testing has been a staple for environments with compliance requirements or high-target value, but has been out of reach for many organizations as a formal effort due to either lack of skills in-house, workload negating it as a priority, or lack of budget to hire an external firm.
“A further extension of these tools has been to add breach testing. Though the ability has been around since the late 1990s, it seemed to have limited adoption in a narrow set of industries until the last roughly two years. At that time, the market went from one player to around eight. The fervor around this technology area has really benefitted technology consumers, allowing them choice and price competition.”
The report reads, “Between 8% and 15% of organizations are not investing in vulnerability management, patch management, and/or penetration testing, with the rest onboard at some level. As seen in the figure, just under 60% of organizations invest less than 15% of their budgets, with 40% investing less than 10%.”
“As breach simulation gains attention, its market penetration will grow significantly and spending in this area will change. Further research will need to be done to separate out each of the four options (penetration testing, vulnerability management, patch management, and breach simulation) to determine how budgets and spending change and whether it increases the overall TAM for the grouping.”
- Will Penetration Testing Disappear?
With the majority of BAS solutions, the attacks occur based on the collected information and are executed in simulation, so no real systems are affected. The rapid expansion in the BAS area is changing the face of vulnerability management, penetration testing, and even patch management.
“EMA does not believe that penetration testing will disappear, but it is likely that for the general consumer, the automated breach simulation will suffice, reducing their risk levels at a value level proportionately higher than hiring a penetration testing firm. Skilled human penetration testers will outperform the automated breach testing in complex attacks for some time, but will be challenged as the vendors continue to build out their attack portfolios,” states the report.
“Breach and attack simulations cost less over time and do not cause outages. Penetration testing is a highly manual activity with expensive labor and is only a snapshot in time. On the other hand, BAS can be run as often as changes are made or new vulnerabilities are reduced, with little to no change in cost. It does not affect production servers since it is a simulation, so no outages are ever incurred.”
Purple Team: Automation + Remediation
HaXM by XM Cyber is the first BAS platform to simulate, validate, and remediate attackers’ paths to your critical assets 24×7. HaXM’s automated purple teaming aligns red and blue teams to provide the full realistic Advanced Persistent Threat (APT) experience on one hand while delivering vital prioritized remediation on the other.
Addressing real user behavior and exploits, the full spectrum of scenarios is aligned to your organization’s own network to expose blind spots. It is executed using the most up-to-date attack techniques safely, without affecting network availability and user experience.
The move to automation empowers organizations with the ability to gain a worm’s eye view into new back doors and blind spots as soon as they appear and move to remediate them immediately, without delay.
Related Topics